Ransom & Dark Web Issues Week 4, Fabruary 2026
ASEC Blog publishes Ransom & Dark Web Issues Week 4, Fabruary 2026 Source code of a South Korean accounting automation solution provider sold on BreachForums Beast ransomware attack targeting a South Korean pharmaceutical company and battery safety component manufacturer [1], [2] Atomsilo resumes activity and
Ransom & Dark Web Issues Week 3, Fabruary 2026
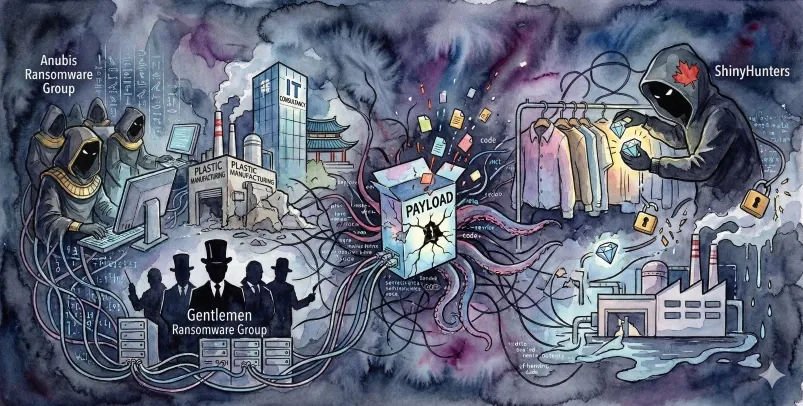
ASEC Blog publishes Ransom & Dark Web Issues Week 3, Fabruary 2026 Anubis and The Gentlemen launch ransomware attacks targeting a South Korean plastics manufacturer and an IT consulting company [1], [2] Emergence of the new ransomware group Payload ShinyHunters claims data breach involving a
January 2026 Security Issues in Korean & Global Financial Sector
This report comprehensively addresses actual cyber threats and related security issues that have occurred in domestic and international financial sector companies. It includes an analysis of malware and phishing cases disseminated targeting the financial sector, presents the top 10 major malware aimed at the financial sector, and provides statistics on
Ransom & Dark Web Issues Week 2, February 2026
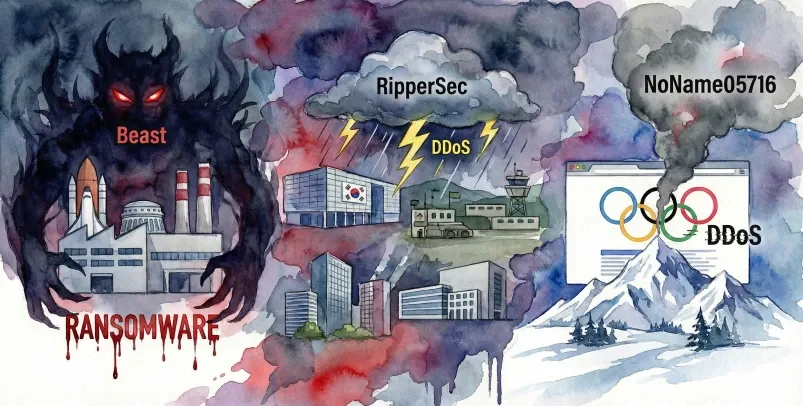
ASEC Blog publishes Ransom & Dark Web Issues Week 2, February 2026 Beast, Ransomware Attack Targeting a South Korean Aerospace Component Manufacturer RipperSec, Claims of DDoS Attacks Targeting South Korean Exhibition Centers, Military Training Grounds, Associations, and Defense-related Companies [1], [2], [3], [4] NoName05716, Claims
January 2026 Threat Trend Report on Ransomware
This report provides the number of affected systems confirmed during January 2026, DLS-based ransomware-related statistics, and notable ransomware issues in Korea and abroad. Below is a summary of some information. The statistics on the number of ransomware samples and affected systems were based on the diagnostic names assigned by AhnLab,
Ransom & Dark Web Issues Week 1, Fabruary 2026
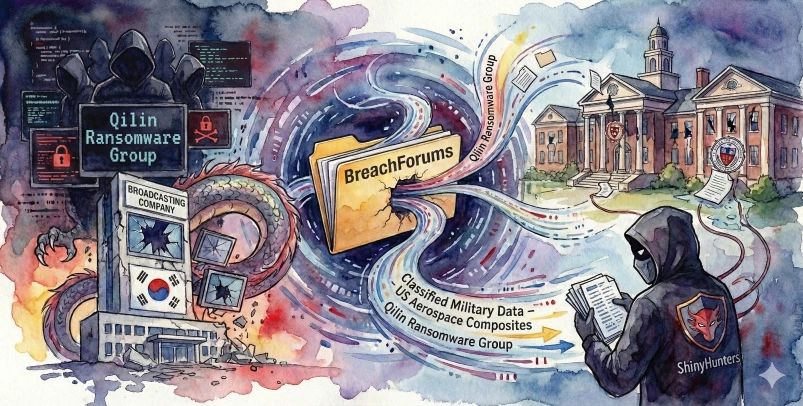
ASEC Blog publishes Ransom & Dark Web Issues Week 1, Fabruary 2026 Qilin Targets South Korean Public Broadcaster with Ransomware Confidential Military Data from U.S. Aerospace Composites Manufacturer Sold on BreachForums ShinyHunters Leaks Data from Two Prestigious U.S. Private Universities
Ransom & Dark Web Issues Week 4, January 2026
ASEC Blog publishes Ransom & Dark Web Issues Week 4, January 2026 New Ransomware Group 0APT and BravoX Identified [1], [2] RAMP Cybercrime Forum Domains Seized by FBI and DOJ World Leaks Targets U.S. Global Sportswear Company in Ransomware Attack
Ransom & Dark Web Issues Week 3, January 2026
ASEC Blog publishes Ransom & Dark Web Issues Week 3, January 2026 Qilin Ransomware Targets Korean Specialist in Semiconductor/Display Components & Surface Treatment U.S. DOJ: Access Broker “r1z” Pleads Guilty Qilin Ransomware Targets Vietnam’s National Airlines
December 2025 Security Issues in Korean & Global Financial Sector
This report comprehensively covers real-world cyber threats and security issues that have occurred in the financial industry in Korea and worldwide. It includes an analysis of malware and phishing cases targeting the financial industry, a list of the top 10 malware strains targeting the industry, and statistics on the sectors
Ransom & Dark Web Issues Week 2, January 2026
ASEC Blog publishes Ransom & Dark Web Issues Week 2, January 2026 Qilin ransomware attack against a Korean automotive smart factory automation equipment manufacturer Customer data of a Korean cloud and hosting service provider shared on DarkForums Everest ransomware attack against a major Japanese automobile